- Home
- ::
- Best Video Conferencing
- ::
- Video Conferencing Features
- ::
- Secure Video Conferencing
Nefsis is Easy to Use and More Secure than Phone, FAX, eMail, or Losing Your Laptop at the Airport
Nefsis was designed for online meetings between multiple
employees, across several offices and the public Internet. For
meetings regarding sensitive topics and private information,
Nefsis offers business-grade secure video conferencing
including meeting passwords, encryption, and signed
certificates (VeriSign).
The Internet community-at-large has long ago established
industry standards for secure communications. Nefsis observes
the same standards used by e-commerce, online retailers and
banks for secure transmission of passwords, credit cards, and
your sensitive data.
![]()
To verify you are in a secure video conferencing session, look for "https:" in
your![]() conference URL, and the padlock symbol in the Nefsis application.
conference URL, and the padlock symbol in the Nefsis application.
For more information, please review the material below, or
feel free to contact us
for a Nefsis design review and
security briefing.
Multi-Layer Security Model
Nefsis uses several techniques to protect your online meetings. Nefsis servers are located in secure facilities with restricted physical access. When enabled, SSL encryption provides transmission security, defeating eavesdroppers and packet sniffers.
Meeting Passwords & Host Controls
Online meeting hosts can select conference passwords, which are required for conference room entry. In addition to password authentication and other technical measures, conference hosts can play video, and personally check every meeting attendee. The host can expel anyone, at anytime.
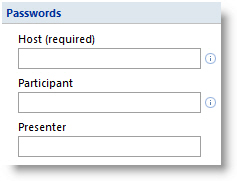
Note: The meeting host can select passwords for just the host and participants (typical); or be more specific, and set separate passwords for the host, presenters, and participants.
Signed Code & Certificates
| This site chose VeriSign SSL for secure e-commerce and confidential communications. | |
| ABOUT SSL CERTIFICATES |
The Nefsis online service uses signed code with a third-party certificate provided by VeriSign. VeriSign is a leading certificate authority and world renown provider of trusted Internet services.
End-to-End Encryption
![]() When the
meeting host selects SSL/TLS Security, Nefsis uses
encrypted connections from end-to-end, including all participants and the
conferencing server. In addition, Nefsis sends all conference data over
one secured TCP/IP connection, ensuring that all data from all features — live data sharing, presentations, voice over the Internet (VoIP), and
video — are all sent over the same encrypted connection.
When the
meeting host selects SSL/TLS Security, Nefsis uses
encrypted connections from end-to-end, including all participants and the
conferencing server. In addition, Nefsis sends all conference data over
one secured TCP/IP connection, ensuring that all data from all features — live data sharing, presentations, voice over the Internet (VoIP), and
video — are all sent over the same encrypted connection.
IT Security Policy, Firewall & Proxy Compliance
Nefsis uses standard ports 80 and 443 for web services, and provides
proxy and firewall traversal in conformance with IT security policies. All
Nefsis conference connections are initiated by the conference user, going
out
their firewall. Nefsis does not attempt any inbound connections.
Nefsis
conferencing operates over one TCP/IP connection, via the physical, NAT
and proxy routing specified by each user’s respective network. Nefsis
supports all leading standards for proxy connections such as TTL values,
plus many vendor specific implementations (e.g., Microsoft ISA
Server) providing the highest possible connection success rates for all
users.
Nefsis conference hosts and participants do not need to concern themselves
with these details, Nefsis secure conferencing just works.
If required, please contact us
for additional details regarding secure video conferencing, firewalls and
proxies.
No Unattended Remote Access Features
All Nefsis conference connections must be initiated by the conference
attendee. In scenarios where Nefsis remote control features are used —
live desktop, application and region sharing — the user is always prompted
with a dialog box requesting remote control. In addition, they are offered
a quick keyboard bail-out hot key that appears on their screen during the
entire remote control session. Nefsis was designed for live conferencing,
there are no unattended remote access or remote control features.
Vendor Questionnaire
The following are some general background questions and recommendations to explore, when considering or evaluating a secure video conferencing vendor.
Does the vendor have a proven product, used by thousands of customers over several years? For sensitive data, this is a must.
What is the vendor's security track record? A few minutes spent doing an Internet
search and some quick checks on popular IT management sites will
highlight any publicized security issues.
Does the vendor or product use proprietary security techniques, or
industry standards? Do they use signed code? In
particular, is their online service a complete implementation, using
public key infrastructure with a third-party certificate authority? Is the CA
a trusted source? Most IT managers insist on industry standard
components, eliminating unknown and potentially dangerous weaknesses.
Signed code, certificates, and well known CAs such as VeriSign, are a
must.
Does the vendor offer a free trial, so that you can verify secure
connections? We recommend testing any secure conferencing service prior
to investing, to confirm security features and standards
compliance.
On-Premise & Private Networks
Please contact us for information regarding on-premise installation and operation over private networks with no access to the public Internet.
Contact Us For Details
![]() For more information, a technical Q&A session, or a live demo of any
of these capabilities, please contact us.
We are happy to answer any questions you may have.
For more information, a technical Q&A session, or a live demo of any
of these capabilities, please contact us.
We are happy to answer any questions you may have.
VeriSign is a registered trademark of VeriSign, Inc. Nefsis is a registered trademark of Nefsis Corporation.
All other trademarks are property of their respective owners.

